Why are computer networks an important part of today’s information technology systems?
Today most businesses use networks to deliver information to employees, suppliers, and customers. A computer network is a group of two or more computer systems linked together by communications channels to share data and information. Today’s networks often link thousands of users and can transmit audio and video as well as data.
Networks include clients and servers. The client is the application that runs on a personal computer or workstation. It relies on a server that manages network resources or performs special tasks such as storing files, managing one or more printers, or processing database queries. Any user on the network can access the server’s capabilities.
By making it easy and fast to share information, networks have created new ways to work and increase productivity. They provide more efficient use of resources, permitting communication and collaboration across distance and time. With file-sharing, all employees, regardless of location, have access to the same information. Shared databases also eliminate duplication of effort. Employees at different sites can “screen-share” computer files, working on data as if they were in the same room. Their computers are connected by phone or cable lines, they all see the same thing on their display, and anyone can make changes that are seen by the other participants. The employees can also use the networks for videoconferencing.
Networks make it possible for companies to run enterprise software, large programs with integrated modules that manage all of the corporation’s internal operations. Enterprise resource planning systems run on networks. Typical subsystems include finance, human resources, engineering, sales and order distribution, and order management and procurement. These modules work independently and then automatically exchange information, creating a company-wide system that includes current delivery dates, inventory status, quality control, and other critical information. Let’s now look at the basic types of networks companies use to transmit data—local area networks and wide area networks—and popular networking applications such as intranets and virtual private networks.
Connecting Near and Far with Networks
Two basic types of networks are distinguished by the area they cover. A local area network (LAN) lets people at one site exchange data and share the use of hardware and software from a variety of computer manufacturers. LANs offer companies a more cost-effective way to link computers than linking terminals to a mainframe computer. The most common uses of LANs at small businesses, for example, are office automation, accounting, and information management. LANs can help companies reduce staff, streamline operations, and cut processing costs. LANs can be set up with wired or wireless connections.
A wide area network (WAN) connects computers at different sites via telecommunications media such as phone lines, satellites, and microwaves. A modem connects the computer or a terminal to the telephone line and transmits data almost instantly, in less than a second. The internet is essentially a worldwide WAN. Communications companies, such as AT&T, Verizon, and Sprint, operate very large WANs. Companies also connect LANs at various locations into WANs. WANs make it possible for companies to work on critical projects around the clock by using teams in different time zones.
Several forms of WANs—intranets, virtual private networks (VPN), and extranets—use internet technology. Here we’ll look at intranets, internal corporate networks that are widely available in the corporate world, and VPNs. Although wireless networks have been around for more than a decade, they are increasing in use because of falling costs, faster and more reliable technology, and improved standards. They are similar to their wired LAN and WAN cousins, except they use radio frequency signals to transmit data. You use a wireless WAN (WWAN) regularly when you use your cellular phone. WANs’ coverage can span several countries. Telecommunications carriers operate using wireless WANs.
Wireless LANs (WLAN) that transmit data at one site offer an alternative to traditional wired systems. WLANs’ reach is a radius of 500 feet indoors and 1,000 feet outdoors and can be extended with antennas, transmitters, and other devices. The wireless devices communicate with a wired access point into the wired network. WLANs are convenient for specialized applications where wires are in the way or when employees are in different locations in a building. Hotels, airports, restaurants, hospitals, retail establishments, universities, and warehouses are among the largest users of WLANs, also known as Wi-Fi. For example, the Veterans Administration Hospital in West Haven, Connecticut, recently added Wi-Fi access in all patient rooms to upgrade its existing WLAN to improve patient access, quality, and reliability. The new WLAN supports many different functions, from better on-site communication among doctors and nurses through both data transmission and voice-over-internet phone systems to data-centric applications such as its Meditech clinical information system and pharmacy management.5
Documenting the Future
Potential customers of Captiva Software didn’t share company cofounder and chief executive Reynolds Bish’s belief that paper wasn’t going away. They held to the idea that personal computers and the internet would make paper disappear, and they weren’t going to invest in software to organize their documents. That almost caused Captiva to go under. “We really were afraid we weren’t going to make it,” said Jim Berglund, an early investor in Captiva and a former board member.
But Bish asked investors for another $4 million commitment—on a bet that paper was here to stay. Bish recalls a board member telling him, “Five years from now people are going to either think you’re a genius or a complete idiot.”
That conversation took place 20 years ago. Captiva Software was named one of the fastest-growing technology companies in San Diego in the early 2000s for its 172 percent increase in revenues. The company was then acquired by EMC Corp.—the sixth-largest software company in the world and top maker of corporate data-storage equipment, with projected annual revenues of more than $9 billion—for $275 million in cash, rewarding embattled early Captiva investors with 10 times their money back. (In 2016, Dell acquired EMC for more than $67 billion.)
Captiva began its journey to the big time in 1989 in Park City, Utah, as TextWare Corp., a small data-entry company. Cofounder Steven Burton’s technical expertise, Bish’s business background, and a credit card helped them get the business going. “It was pure bootstrapping,” Bish said. “We did everything from going without a salary for a year or more to using up our credit cards.”
Bish and Burton quickly saw the need for employees to enter data more directly and accurately. The software they developed still required clerks to type information from a paper document, but it could check for inaccuracies, matching zip codes to cities, for instance. In 1996, TextWare produced software that could “read” typewritten words on a scanned piece of paper, which significantly reduced the number of data-entry clerks needed. It found popularity with credit-card processors, insurance companies, shipping companies, and other corporations that handled thousands of forms every day.
TextWare acquired or merged with five firms, went public, changed its name twice, and in 1998 set up its headquarters in San Diego, California, after buying Wheb Systems, which is based there. In 2002, the company merged with publicly held ActionPoint, a San Jose, California, document-processing company, and changed its name to Captiva.
An estimated 80 percent of all information is still paper-based, according to market research firm Forrester Research. Captiva’s flagship products, InputAccel and FormWare, process over 85 million pieces of paper worldwide every day, leaving no doubt that Bish’s vision was on target. Paper is indeed here to stay.
Sources: “Why Captiva?” https://www.emc.com, accessed February 21, 2018; EMC corporate website, “About Us,” https://dellemc.com, accessed February 21, 2018; “Lucera Uses Connectivity Routes of Chicago, New York, London and Tokyo as a Trading Hub in Trading Increases,” BSO, https://www.bsonetwork.com, October 19, 2017; Ron Miller, “$67 Billion Dell–EMC Deal Closes Today,” Tech Crunch, https://techcrunch.com, September 7, 2016; Brian Sherman, “Input Management and Opportunities for the Reseller Channel: An Interview with Wayne Ford, VP of Partner Alliances at Captiva,” ECM Connection, http://www.ecmconnection.com, December 27, 2005; Kathryn Balint, “Captiva’s Paper Chase Paying Off,” San Diego Union-Tribune, December 9, 2005, pp. C1, C5.
Critical Thinking Questions
- What role did co-founders Reynolds Bish and Steven Burton play in the evolution of tiny TextWare into hugely successful Captiva?
- What other unique factors were responsible for the company’s remarkable growth?
An Inside Job: Intranets
Like LANs, intranets are private corporate networks. Many companies use both types of internal networks. However, because they use internet technology to connect computers, intranets are WANs that link employees in many locations and with different types of computers. Essentially mini-internets that serve only the company’s employees, intranets operate behind a firewall that prevents unauthorized access. Employees navigate using a standard web browser, which makes the intranet easy to use. They are also considerably less expensive to install and maintain than other network types and take advantage of the internet’s interactive features such as chat rooms and team workspaces. Many software providers now offer off-the-shelf intranet packages so that companies of all sizes can benefit from the increased access to and distribution of information.
Companies now recognize the power of intranets to connect employers and employees in many ways, promoting teamwork and knowledge-sharing. Intranets have many applications, from human resource (HR) administration to logistics. For instance, a benefits administration intranet can become a favorite with employees. Instead of having to contact an HR representative to make any changes in personnel records or retirement plan contributions or to submit time sheets, staff members simply log on to the intranet and update the information themselves. Managers can also process staffing updates, performance reviews, and incentive payments without filing paperwork with human resources. Employees can regularly check an online job board for new positions. Shifting routine administrative tasks to the intranet can bring additional benefits such as reducing the size of the HR department by 30 percent and allowing HR staff members to turn their attention to more substantive projects.6
Enterprise Portals Open the Door to Productivity
Intranets that take a broader view serve as sophisticated knowledge management tools.
One such intranet is the enterprise portal, an internal website that provides proprietary corporate information to a defined user group. Portals can take one of three forms: business to employee (B2E), business to business (B2B), and business to consumer (B2C). Unlike a standard intranet, enterprise portals allow individuals or user groups to customize the portal home page to gather just the information they need for their particular job situations and deliver it through a single web page. Because of their complexity, enterprise portals are typically the result of a collaborative project that brings together designs developed and perfected through the effort of HR, corporate communications, and information technology departments.
More companies use portal technology to provide:
- A consistent, simple user interface across the company
- Integration of disparate systems and multiple sets of data and information
- A single source for accurate and timely information that integrates internal and external information
- A shorter time to perform tasks and processes
- Cost savings through the elimination of information intermediaries
- Improved communications within the company and with customers, suppliers, dealers, and distributors
No More Tangles: Wireless Technologies
Wireless technology has become commonplace today. We routinely use devices such as cellular phones, mobile devices, garage door openers, and television remote controls—without thinking of them as examples of wireless technology. Businesses use wireless technologies to improve communications with customers, suppliers, and employees.
Companies in the package delivery industry, such as UPS and FedEx, were among the first users of wireless technology. Delivery personnel use handheld computers to send immediate confirmation of package receipt. You may also have seen meter readers and repair personnel from utility and energy companies send data from remote locations back to central computers.
Bluetooth short-range wireless technology is a global standard that improves personal connectivity for users of mobile phones, portable computers, and stereo headsets, and Bluetooth wirelessly connects keyboards and mice to computers and headsets to phones and music players. A Bluetooth-enabled mobile phone, for example, provides safer hands-free phone use while driving. The technology is finding many applications in the auto industry as well. Bluetooth wireless technology is now standard in many vehicles today. Many car, technology, and cell phone companies—among them Amazon, Apple, Audi, BMW, DaimlerChrysler, Google, Honda, Saab, Toyota, and Volkswagen—already offer Bluetooth hands-free solutions. Other uses include simplifying the connection of portable digital music players to the car’s audio system and transferring downloaded music to the system.7
Private Lines: Virtual Private Networks
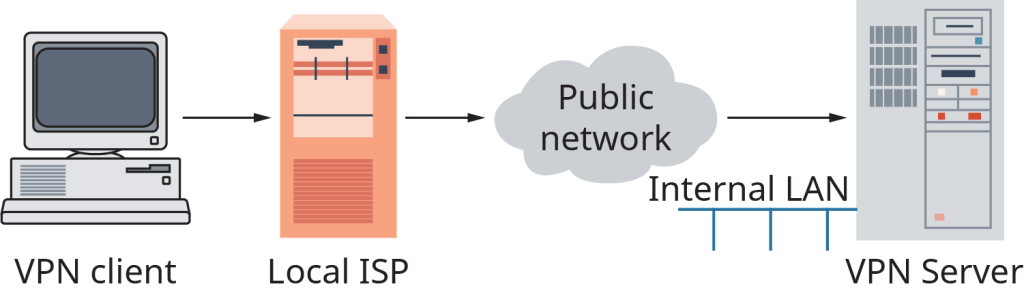
Many companies use virtual private networks to connect two or more private networks (such as LANs) over a public network, such as the internet. VPNs include strong security measures to allow only authorized users to access the network and its sensitive corporate information. Companies with widespread offices may find that a VPN is a more cost-effective option than creating a network using purchased networking equipment and leasing expensive private lines. This type of private network is more limited than a VPN, because it doesn’t allow authorized users to connect to the corporate network when they are at home or traveling.
As Exhibit 13.4 shows, the VPN uses existing internet infrastructure and equipment to connect remote users and offices almost anywhere in the world—without long-distance charges. In addition to saving on telecommunications costs, companies using VPNs don’t have to buy or maintain special networking equipment and can outsource management of remote access equipment. VPNs are useful for salespeople and telecommuters, who can access the company’s network as if they were on-site at the company’s office. On the downside, the VPN’s availability and performance, especially when it uses the internet, depends on factors largely outside of an organization’s control.
VPNs are popular with many different types of organizations. Why? Security is one of the main reasons to always use a VPN to access the internet. Because all your data is encrypted once tunneled, if a hacker were trying to intercept your browsing activity, say, while you were entering your credit card number to make an online purchase, the encryption would stymie their efforts. That’s why it’s a particularly good idea to use VPNs in public settings such as coffee shops and airports.8
Software on Demand: Application Service Providers
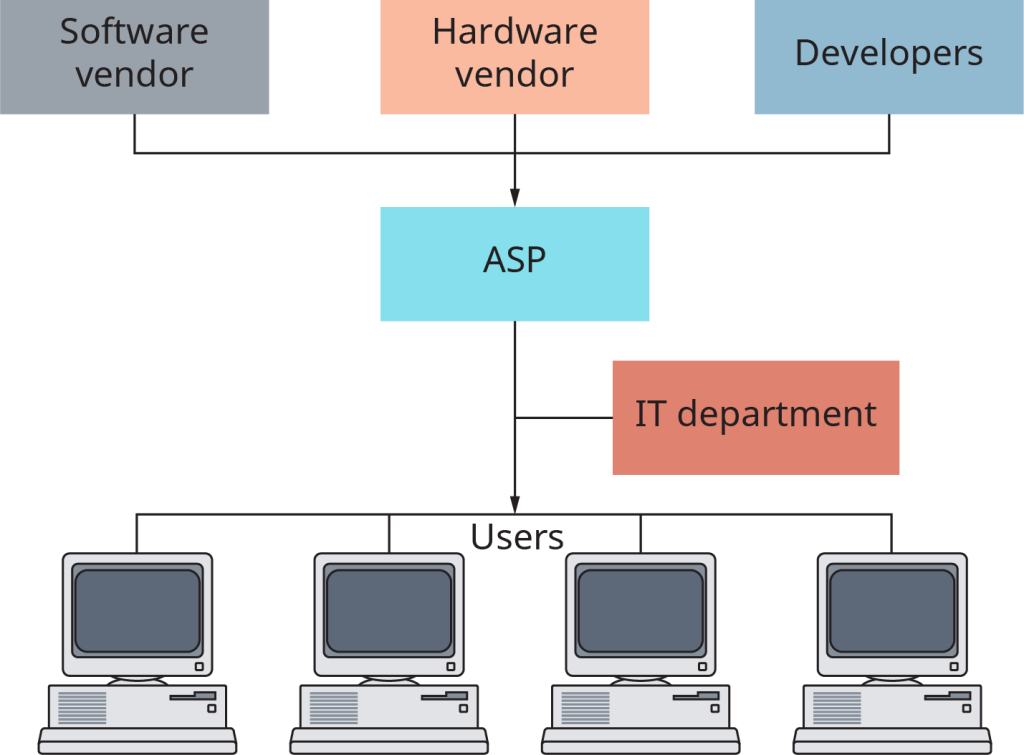
As software developers release new types of application programs and updated versions of existing ones every year or two, companies have to analyze whether they can justify buying or upgrading to the new software—in terms of both cost and implementation time. Application service providers (ASP) offer a different approach to this problem. Companies subscribe, usually on a monthly basis, to an ASP and use the applications much like you’d use telephone voice mail, the technology for which resides at the phone company. Other names for ASPs include on-demand software, hosted applications, and software-as-a-service. Exhibit 13.5 shows how the ASP interfaces with software and hardware vendors and developers, the IT department, and users.
The simplest ASP applications are automated—for example, a user might use one to build a simple e-commerce site. ASPs provide three major categories of applications to users:
- Enterprise applications, including customer relationship management (CRM), enterprise resource planning, e-commerce, and data warehousing
- Collaborative applications for internal communications, e-mail, groupware, document creation, and management messaging
- Applications for personal use—for example, games, entertainment software, and home-office applications
According to recent surveys, more companies are currently using an ASP, and even moving their legacy systems to the cloud. Estimates suggest revenues from subscriptions to on-demand cloud services were about $180 billion in 2017. This sector is growing much more rapidly—three times faster—than traditional hardware and software.9 As this market grows, more companies are adding on-demand offerings to their traditional software packages. Amazon (Amazon Web Services), IBM, Microsoft, and Salesforce.com are among the leading cloud service providers.10
Until recently, many companies were reluctant to outsource critical enterprise applications to third-party providers. As ASPs improved their technologies and proved to be reliable and cost-effective, attitudes have changed. Companies, both large and small, seek cost advantages such as the convenience ASPs provide. The basic idea behind subscribing to an ASP is compelling. Users can access any of their applications and data from any computer, and IT can avoid purchasing, installing, supporting, and upgrading expensive software applications. ASPs buy and maintain the software on their servers and distribute it through high-speed networks. Subscribers rent the applications they want for a set period of time and price. The savings in licensing fees, infrastructure, time, and staff are significant.
Managed service providers (MSP) represent the next generation of ASPs, offering greater customization and expanded capabilities that include business processes and complete management of the network servers. The global market for managed IT services reached $149.1 billion in 2016. This market is estimated to reach $256.5 billion in 2021, from $166.7 billion in 2017, at a compound annual growth rate of 11.5 percent for the period 2018 through 2021.11
- What is a computer network? What benefits do companies gain by using networks?
- How do a LAN and a WAN differ? Why would a company use a wireless network?
- What advantages do VPNs offer a company? What about the cloud, ASPs, and MSPs?