10.7 Cybercrime
Brandon Hamann

Iphone.
TikTok.
Spotify.
SmartWatch.
WiFi.
Google.
Shein.
Hospitals.
Subway Rewards.
Chik-Fil-A App.
This class.
What do they all have in common? They all have your personal information in some form or fashion stored somewhere digitally in a “secure” location. Oh sure, they say it’s “safe,” but is it? At any given moment, someone is trying to get into the sensitive areas of everyone of those listed places above to try and take the personal information that you have entered to try and steal your identity for the purposes of an illegal act. They will then sell it to whoever will buy it, and that individual will create a persona using your information to open credit cards, bank accounts, make purchases, and ruin your good credit and reputation that you have worked so hard for years. And all these criminals need to do it are a computer and an Internet connection. Welcome to the Age of Cybercrime.
Cybercrimes are any illegal acts committed using a communication device. It’s a relatively new phenomenon, but the crimes are not. They are the same crimes, just repackaged using new methods. Identity Theft is still theft. Crypto and Digital Currency Robbery is still Robbery. Technological advancements, the Internet, and our willingness to be open and free with the sharing of our personal information makes it that much easier for criminals to take advantage of the large amount of data that is out there, ripe for the taking. But criminals aren’t the only ones using our information for nefarious things. Corporations, advertising and marketing firms, and even governments use the same information we provide to tailor experiences and goods and services based on our everyday activities.
But how did it all start? Watch the trailer below to begin that journey.
The movie was “War Games.” It was released in 1983. Aside from it being old and one of my favorites growing up, it was important for its time because of who it influenced. President Ronald Reagan watched this movie while on vacation at Camp David and he was so intrigued by the movie’s thematic presence that he would immediately call a meeting of his top military advisors and ask the question “Is this possible?” (Kaplan, 2016). The movie involves a high school youth who just wants to play some video games so he uses the Internet at the time to “hack into” what he thinks is a new gaming company. What he doesn’t realize is that what he unintentionally does is begin communicating with a Top-Secret military computer that simulates Global Nuclear scenarios deep inside a military installation. Ultimately the computer must learn the difference between what is real and what is just a game as the fate of world is in the balance.
It sounds extremely far-fetched, but the reality of it is it really isn’t. The Internet, for example, started out as a U.S. government communications project used to share sensitive information between research teams across great distances. It was easier to transmit data through phone lines and print them out on the other end than to mail them and risk exposure to being captured by an enemy state. What the U.S. government learned unexpectedly was that they could also intercept that same data from foreign governments without being detected (initially) and so the great Cyber Race began.
And then came the cellphones, and personal computers, and the Worldwide Web. Suddenly, the government no longer had a monopoly on the digital frontier, but they could still listen in undetected. That is until lawmakers began passing legislation guaranteeing the privacy of digital information for American citizens. The first such law passed was in 1986 with the Electronic Communications Privacy Act. While it banned eavesdropping on personal spoken communications, it did not provide protections for email and other telephone communications. To learn more about the evolution of digital privacy laws, check out this website.
The Evolution of Cybercrime
As the Internet became more of a “thing” and people became more connected with each other through their digital personalities, the opportunities for crime also exponentially increased. As mentioned earlier, the crimes did not change, just the means by which they were committed. Robbery and theft no longer had to be face-to-face. They could be perpetrated simply by using a bit of code and a phone line connection to the Internet. Thieves didn’t have to physically be in the building to steal anything of value if they had the means to get passed the online security.
Electronic mail (E-mail) and Texting have morphed into new communication services that criminals are using to scam would-be victims. Phishing and Smishing are new methods of information gathering that are illegal and can trick a person into thinking that they are interacting with a legitimate service providers, unbeknownst to them they are being preyed upon by identity thieves.
Cybercrimes also include bullying and harassing messages sent through social media and other digital platforms. They can also include cyberstalking, as well as many others. Some other common cybercrimes include:
- Ransomware – personal data is encrypted and unusable until a a payment is made to gain access
- Hacking – unauthorized use electronic equipment for the sole purpose of gaining access to restricted information
- Fraud – bank theft, misuse of personal information, theft of services
- Software Piracy – illegal possession of software by a violation of copyright or license restrictions
- Cyber Extortion – DDOS (Direct Denial of Service)
Cybercrimes and the Criminal Justice System
There really isn’t much to say about cybercrimes when it comes to the criminal justice system. As mentioned before, the crimes don’t change, just the method of how they are committed. The real problem comes in how they are investigated and apprehended. Law enforcement agencies now have to get creative in their investigative practices because cyber criminals are much more “tech savvy” in their approach to crime. Special teams need to be created to attempt to track these violators who are experienced in the same methods the criminals are using to commit their crimes. Computer programmers, computer scientists, financial experts, forensic accountants, social media consultants, etc. are all being utilized in an effort to stay up-to-date with all the new ways in which criminals are carrying out their schemes.
Cybercrime in Louisiana
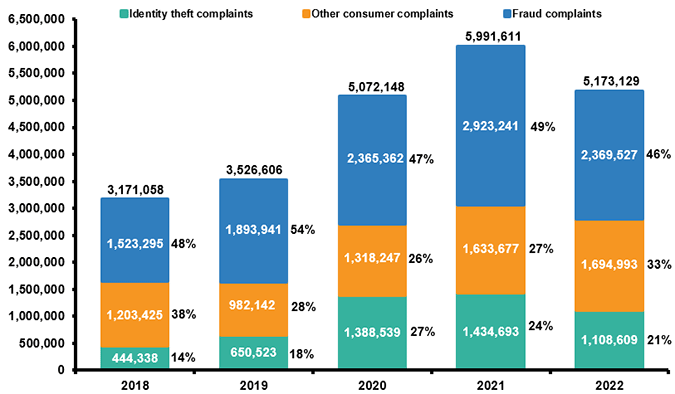
The chart above illustrates a nationwide problem with cybercrime as it pertains to identity theft and fraud. According to statistics, on a year-to-year basis, these crimes are steadily increasing. Louisiana is no stranger to cybercrimes, either. In 2022, Louisiana ranks 2nd with almost 25,000 reports (534 per 100,000) of identity theft (iii.org, 2022) alone. So what can be done?
The Louisiana State Police in cooperation with LSU have started to Artificial Intelligence (AI) to track cybercrime. Researchers have developed a new tool, HookTracker, to look for potential malware programs and track them back to their origin points. This would allow investigators to catch would-be cyber criminals and gain valuable evidence to be used in prosecutions. To read more about HookTracker and Artificial Intelligence in the fight against Cybercrime, read this article.
the fraudulent practice of sending emails or other messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
the fraudulent practice of sending text messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords or credit card numbers.

